APT, Advanced Persistent Threat, is usually a state/nation sponsored threat or sometimes a private consultancy service provoke this threat, targeting individual users(high profiles) or preferably a country. They sneak into our system via the network. These threads remain in our system for years, possibly decades too. The main aim of APT is to get all the information from the target without the user knowledge. Even the latest firewall/antivirus would fail to prevent this attack.
The main drawback of all the APT's/threat is they require user interaction in order to gain access to our system. This is mostly done through phishing attacks.

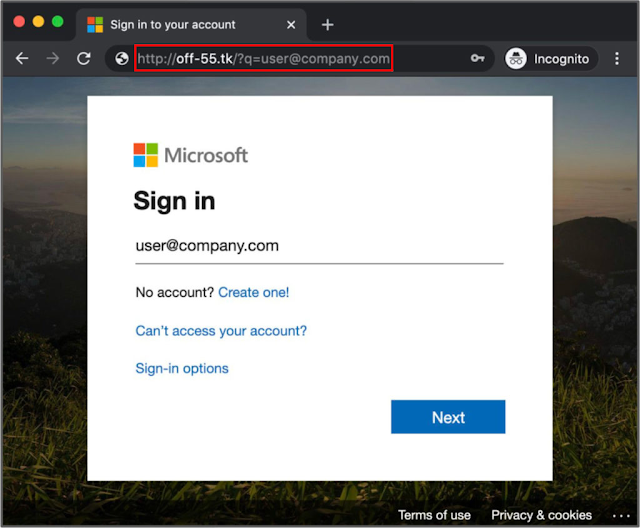
Phishing: A threat actor gathers the target's information using publicly disclosed, social media or through breached websites. Threat agents use this information to obtain your PID like email, phone number, Date of birth, Location, Address, your interests, The ads you clicked online and so on. Keeping this details they usually create a link and sent you over mail/SMS. Once you click them you are then redirected to a webpage. This webpage is actually a false page created by thread actors to gather more information. The webpage will be similar to Facebook login page, Instagram page, office portal login page or it might be even your firewall login. The user pretends that it is legitimate and falls as a victim by providing all the details. This technique was used by the threat actors in the China to gather information about 140 companies in the US alone. A sample Phishing attack is shown below
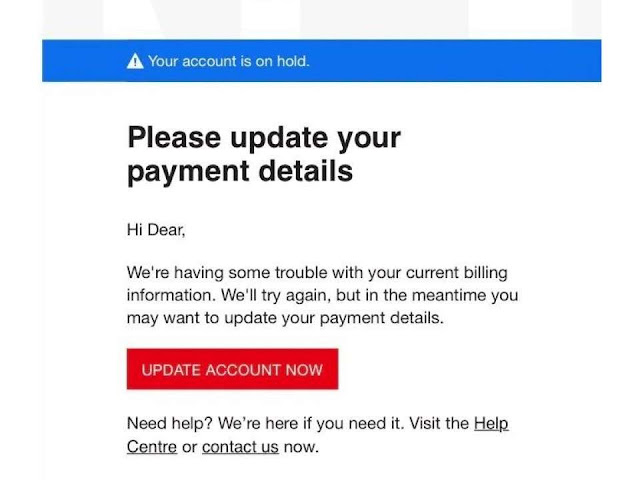
We have provided a sample test case of how attackers create a fake page and steal your data. Always remember to watch URL and check your receipt and mail address thoroughly without compromising your mind.
The Greater Impact
APT-1 targeted attackers were English-speaking countries. Mandiant(Fireye) who discovered this cyber espionage attack has confirmed that the group has stolen 6.5 TB of data from 141 companies till 2011. This includes Proprietary documents, blueprints, employee details, database details about the company, and signed business copies with their clients.
In 2011 this threat actor has compromised 14 companies in 11 months of time, mind-blowing. They also compress all the files in a 200 MB, so that the user gets less attention to those files. Once the data is transferred from the victim computer the file is then shredded.
Mandiant however discovered that this attack was a Chinese state sponsored attack and most of the IP address was located from Shanghai. They also opened new Webmail accounts to send Phishing mails. They initially opened a mail address using some randomly generated name and started to open mail accounts from the compromised data.
Mandiant discovered the cyberespionage location which was located near Pudong, Shanghai, China. This group consists of three major human activities which proficient English speakers to engage in this attack.
Their attack methodology is so simple, they create a webmail accounts and sends it to the victim. Once they click them they become a victim and these actors will start to create a backdoor way to access the victim's system. Mandiant faced major difficulties in closing the backdoor, where if Mandiant closes one background they immediately create another backdoor to transfer files. This was a challenging task to find and close 'em all. Even the attackers used different kinds of backdoor for the individual machine. But Mandiant somehow managed to find their heart and kill all the backdoors available.
How Mandiant Confirmed
- The Attackers' location was spread into china, but two major groups remained near the PLA unit.
- Chinese government laid a fiber optic cable in the newly constructed building with special permissions.
- Unit 61398 is specially trained for computer networking activities and fraud commitments.
- The webmail account was created from China and the data gathered from the victim are redirected to China using some jump servers.
- Chinese build a mass infrastructure inside and this was the one of the top 5 priorities in their budget announcements at that time.
- Google china was also shut down and Baidu was created at the same time.
- Around 700 IPs are registered from China for this activity.
- They have used Microsoft keyboards with simplified Chinese translation.
- 817 remote desktop connection retraced to China.
- 614 unique IP address were used for HTRAN Communications.
The Real Attackers
Hackers don't use real names instead they represent themselves using virtual names like ugly bear, Legion of doom, Lizard ball, etc., In APT-1 three names were discovered in 2011. This was discovered when they released their APT-1 tools over the public platforms.
1. Comment Crew
2. Comment Group
3. Shady rat
Conclusion
Always stay precautious while opening unverified mails. Investigate the received mail address before opening. Always ask the concert person to verify the documents. Patch your updates regularly. Use separate network for your office and personal use. Stay updated to news. Use incognito mode and temp mail whenever possible.









Comments